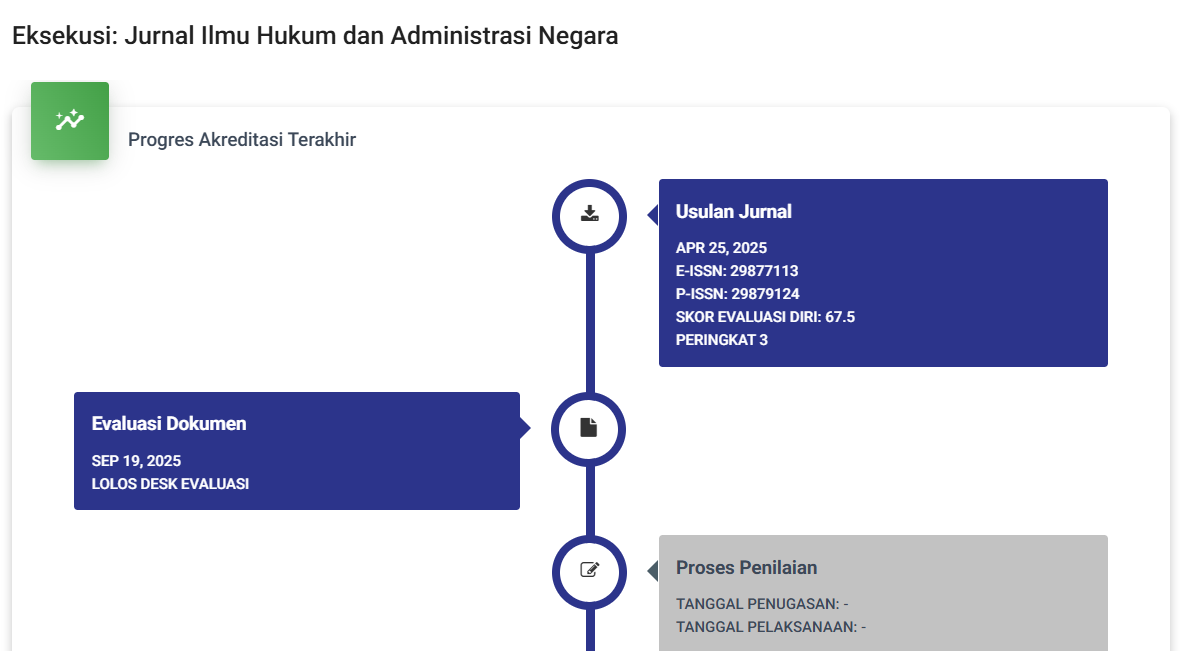
Perlindungan Data Pribadi dalam Kasus Ransomware: Apa Kata Hukum?
DOI:
https://doi.org/10.55606/eksekusi.v2i4.1823Keywords:
Law, Personal Data Protection, Ransomware CaseAbstract
Ransomware attacks are an increasingly complex and costly global threat. International reports show a 300% increase in the frequency of ransomware attacks in the last five years (for example, data from IBM Security or Kaspersky). This threat not only blocks data access through encryption, but also jeopardizes privacy. This research will also examine the criminal law aspects associated with ransomware attacks, including the possible prosecution of the perpetrators of the attacks and the legal liability for victimized organizations. The theoretical study in the research titled "Personal Data Protection in Ransomware Cases: What Does the Law Say?" covers the theory of legal protection of personal data. The research method uses normative legal research that examines applicable regulations, namely the Criminal Code, ITE Law, PDP Law. This research refers to the case of a ransomware attack that hit Bank Syariah Indonesia (BSI), where the Lock Bit hacker group managed to steal the personal data of more than 15 million customers. This attack resulted in significant operational disruption to the bank's services. Ransomware is categorized as an act of extortion in accordance with Article 368 of the Criminal Code and Article 27 paragraph (4) of the ITE Law. The ITE Law and the Criminal Code are not considered to specifically regulate ransomware, although the articles (such as extortion and hacking) can be used to ensnare the perpetrators Collaboration between the government, the private sector, and the cybersecurity community is needed to build an early detection system for ransomware threats.
References
Afifah, D. (2023). Perlindungan konsumen di sektor jasa keuangan pada kasus serangan siber ransomware yang menimpa perbankan. JIIP - Jurnal Ilmiah Ilmu Pendidikan, 6(11), 9318–9323. https://doi.org/10.54371/jiip.v6i11.3176
Annisa, S., Langi, A. R., Padang, U. N., & Terbuka, U. S. (2025). Evaluasi strategi reaktif pasca serangan ransomware pada pusat data nasional sementara 2 Surabaya 1. Prosiding Seminar Nasional Sains dan Teknologi Seri III, 2(1), 680–691.
Aruan, J. E. S. (2024). Perlindungan data pribadi ditinjau dari teori perlindungan hukum dan teori perlindungan hak atas privasi. Jurnal Globalisasi Hukum, 1(1), 1–22. https://doi.org/10.25105/jgh.v1i1.19499
Ferdiansyah. (2018). Analisis aktivitas dan pola jaringan terhadap Eternal Blue dan WannaCry ransomware. JUSIFO (Jurnal Sistem Informasi, 2(1), 44–59. http://eprints.binadarma.ac.id/3873/1/Ferdiansyah-Analisis Aktivitas dan Pola Jaringan Terhadap Eternal Blue dan Wannacry Ransomware.pdf
Hartati, C. S., & Muhammad, A. (2023). Combating cybercrime and cyberterrorism in Indonesia. Jurnal Hubungan Internasional, 11(2), 45–56. https://doi.org/10.18196/jhi.v11i2.15647
Jurnal, D., Ilmu, D., Pembangunan, U., Veteran, N., & Upnvj, J. (2023). Hukum pertahanan dan keamanan negara: State defense and security law. Jurnal Dunia Ilmu Hukum dan Politik, 1(4), 56–67. https://doi.org/10.59581/doktrin.v1i4.1355
Mubarak, A. S., Insirat, M. N., & Lutfiya, M. N. (2024). Ransomware: Evolution, classification, attack phase, detection, and prevention. Seminar Nasional Teknik Elektro, Sistem Informasi, dan Teknik Informatika, 1–6.
Muhaimin, S., & Cokroaminoto, J. H. O. S. (2025). Analisis serangan ransomware pada sistem keamanan siber Bank Syariah Indonesia (BSI) terhadap customer trust. Journal Transformation of Mandalika, 6(2), 67–72. https://doi.org/10.56741/bst.v2i02.353
Novita, A. P., Fatmanegara, F., Runtuwene, F. J. J., Samuela, J. T., & Syahbani, M. F. (2023). Cyber security threats: Analisis dan mitigasi risiko ransomware di Indonesia. Jurnal Ilmiah Sistem Informasi, 3(1), 160–169. https://doi.org/10.46306/sm.v3i1.91
Prayugah, M. I., Indahyanti, U., & Ariyanti, N. (2024). Analisis sentimen publik pada pemerintah dalam serangan ransomware dengan pendekatan SMOTE. JOISIE (Journal of Information Systems and Informatics Engineering, 8(2), 333–343. https://doi.org/10.35145/joisie.v8i2.4764
Ramadhan, G. (2023). Perlindungan hukum bagi korban ransomware WannaCry tindak pidana ransomware. Jurnal Kajian Kontemporer Hukum dan Masyarakat, 1(2), 1–15. https://doi.org/10.11111/dassollen.xxxxxxx
Simorangkir, A. (2024). Ransomware pada data PDN: Implikasi etis dan tanggung jawab profesional dalam pengelolaan keamanan siber. Kampus Akademik Publishing, 2(6), 324–331. https://doi.org/10.61722/jssr.v2i6.2966
Sulistiadi, & Salman, M. (2023). Ransomware attacks threat modeling using Bayesian network. Digital Zone: Jurnal Teknologi Informasi dan Komunikasi, 14(1), 43–56. https://doi.org/10.31849/digitalzone.v14i1.13788
Wahidin, G. W., Syaifuddin, S., & Sari, Z. (2022). Analisis ransomware WannaCry menggunakan aplikasi Cuckoo Sandbox. Jurnal Repositor, 4(1), 83–94. https://doi.org/10.22219/repositor.v4i1.1373
Yuniarti, D. R., Alfarizy, H. F., Siallagan, Z., & Rizkyanfi, M. W. (2023). Analisis potensi dan strategi pencegahan cyber crime dalam sistem logistik di era digital. Jurnal Bisnis, Logistik dan Supply Chain (BLOGCHAIN, 3(1), 23–32. https://doi.org/10.55122/blogchain.v3i1.714